A Beautiful Day at Cascadia College
Cascadia College is a beautiful campus, and just strolling to the event felt refreshing—a nice mental reset before the day began.

On Speaking & Cybersecurity

One big realization from this event? I really love talking about cybersecurity. It’s not just a professional interest; it’s a topic I can talk about endlessly. I think I felt more at peace than I do when performing music.
I might have been a little chatty—not out of nervousness, but because I was genuinely excited. Public speaking isn’t new to me, but this talk made me realize that when I get the floor to discuss something I’m truly passionate about, it lights me up. And honestly? I want more of that.(Pic of Me @ the Talk)
Preparing for the Talk
When I first looked at the Climate Week agenda, I noticed there was a wide range of topics. I wanted to choose something that felt relevant both to me and the event. While there were a few tech-focused talks, I wanted to carve out a cybersecurity perspective—one that would resonate with engineers, managers, and leaders alike.
I researched recent cyberattacks targeting critical infrastructure—everything from the maritime sector to agriculture—and dug into trends like AI red team innovations. My main takeaways were:
- The scope of cybersecurity in these sectors is huge.
- A deeply technical talk could easily get bogged down in jargon or command-line details.
- I wanted to show a bigger-picture model of how all of this fits together.
That’s when I decided to create a demo app—a simple dashboard simulating AI-driven sensors.
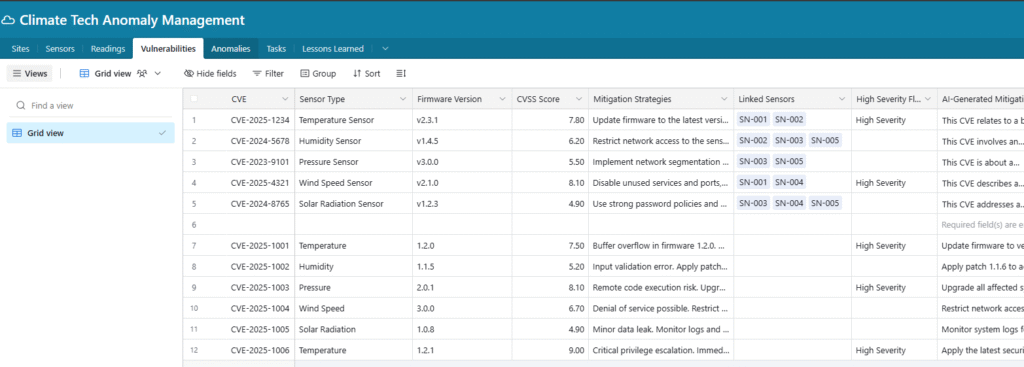
Airtable – Climate Tech Anomaly Management (Link)
Realizations from using this tool became the foundation of my talk and the point where I began to see the deeper intersections of AI, operational technology (OT), security, IT, and real-world risks.
The Reality of IT and OT Convergence
Based my research, AI is primarily being used to aggregate sensor data, helping technicians, managers, and leaders make faster, smarter decisions—everything from scheduling repairs to deploying software updates.
But there’s a big challenge: The quality and security of that data are becoming interdependent.
What I noticed first:
- A disruption in OT (like faulty sensors or manipulated events) can affect IT/AI systems.
- IT vulnerabilities can corrupt the data feeding AI models, leading to disruptions (more time checking bad data)
Then I started to reflect on my past panel talks on IT/OT Convergence (in short, IT/OT roles and technologies blending together).
Today, AI handles much of the aggregation, but the human responsibility for ensuring safety and accuracy hasn’t gone away. And it’s a core staple of using AI in OT/ICS systems.
This model has been a two-way street: I’m reminded me of older alarm system response plans where humans had to interpret every alert.
When technology became more prevalent in crime response, at some point: the sensors providing bad information DID become an issue for emergency response. Resulting in wasted times, costs, and efficiency. This risk is STILL present with AI Integration, making the human validation component more important – because we’re trusting a system that is known to hallucinate data – with the weight to factor our decisions.
(Article References)
How AI Is Helping Power Suppliers in the Energy & Utilities Sector | BizTech Magazine
Grid Modernization Initiative | Department of Energy (DoE’s Grid Improvements – Utilizing AI)
On IT/OT Convergence
When I think about the future of AI, I see IT and OT convergence as a major pillar of operational risk. We have to ask ourselves:
- How will the data we use impact physical systems?
- How can physical disruptions affect the integrity of our data?
Sometimes the consequences of cyberattacks are immediate, but other times they play out over weeks or months—like identity theft that slowly erodes someone’s financial stability and reputation.
There could be a loss of commodity resources because of an IT based cyberattack ON an ICS system. Threat actors may be able to alter physical phenomena to feed back data into the sensors, for AI to utilize within a contained information system; or they might be able to impact the AI’s ability to accurately portray information.
Feedback from the Talk
Speaking
I live-streamed my talk to some close friends, and they told me they learned something new and valuable. That kind of feedback means a lot to me.
I could’ve been less excited – but I think that’s obvious.
Content
In-person, my audience included a grant writer, an administrative officer, a developer/technician, and an AI engineer. I took a high-level, risk-based approach, which I think worked, but it wasn’t as technical as some may have expected.
A few people mentioned that the title of my talk didn’t quite match the content. I completely agree. Titling isn’t my strong suit (working on it!), but it’s something I want to improve because it sets expectations for the audience.
A title like: “Mitigating Proactive Risk: A Review of the AI’s use-case in IT/OT Climate Sensitive Environments” – would’ve been better
What I’d Do Differently Next Time
I’ll be honest—I didn’t have a ton of time to review the speaker list before this talk, which might have helped me tailor my approach. I’d love to take it a step further next time—maybe showing AI red team tools in action on climate-based sensors or even modeling an attack scenario.
Still, I’m proud of the perspective I delivered. My goal was to emphasize that while technology might seem straightforward to us as professionals, we also need to ensure that the people using it alongside us are equally safe and informed while using AI. And that the people using AI in technology that could affect us as humans, are proactively considering risk.
Closing Thoughts
Due to the titling, I suspect some attendees expected a more technical session—like sensor-level deep dives or AI troubleshooting steps. Instead, I presented a broader narrative: how climate, technology, and people intersect, and how AI is being leveraged to enhance our lives while introducing new risks that we must address.
This talk has motivated me to keep refining how I present these ideas. And honestly? I can’t wait for the next one.
Shout out to Anquida Adams with ALA Consulting Firm & PNW Climate week for having me.
(Here’s a link to the speaker slides)
To inquire about Turnstone Compliance or any services that we offer, please contact us at our website.


